Compliance
Services

Our compliance services cover a range of controls related to inventory, data flow mapping, cybersecurity policies, risk assessment, access management, data protection, business continuity, workforce training, vulnerability scans, event triage, and incident response.
Read more…
Data Governance Tools

We offer tools to support data governance and assessment services for various standards such as PCI-DSS, ISO/IEC 27001, CMMC, NIST-CSF, SP800-53, SP800-171, HIPAA, SOC2, GDPR, CCPA, and more.
Read more…
Real-Time Threat Response

EUS clients use a real-time monitoring system that alerts highly competent staff to investigate potentially suspicious actions often used by threat actors. These 24x7x365 Security Operations Centers are an important part of overall threat defense.
Read more…
Multi-Cloud Computing

Multi-cloud refers to the use of cloud services from multiple cloud vendors, allowing organizations to run applications on different platforms. This approach offers flexibility, cost savings, and risk reduction. Multi-cloud solutions are built on open-source technologies and include capabilities for managing workloads across multiple clouds.
Read more…
Business Continuity Planning

On any given day the weather, other natural disasters, or even malicious threat actors can present your business or organization with costly disruptions. Implementing and testing contingency plans and backup systems before a disruption or disaster occurs is vital to timely recovery efforts.
Read more…
SDWAN – WAN Optimization
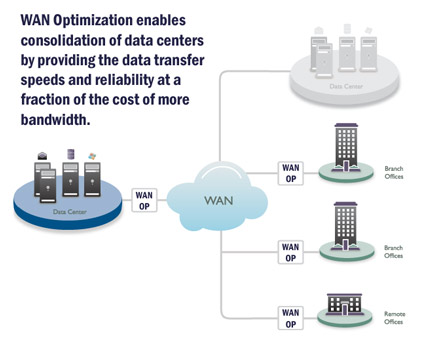
The legacy WAN is expensive, data center dependent, and offers unpredictable application performance. WAN Optimization (WAN OP) and Software-Defined Wide Area Network (SD-WAN) have evolved to address these issues..
Read more…
Pillars of our work:
Please tap or click the headings for detail of each pillar.
Cybersecurity: intrusion prevention
Technology tools, expert security staff, 24x7x365 monitoring and adherence to security policy are used to accomplish this objective. We help you implement mechanisms to monitor organizational systems for attacks and indicators of potential attacks, as well as unauthorized access and use. Vulnerability and penetration testing are used to validate best practices are being used.
Business continuity and resilience
These can be achieved if systems are designed from the start to be fault tolerant and contingency plans are made, tested and updated. We can help implement control requirements related to having immutable backups, performing comprehensive backups, regularly testing data backups, and protecting the confidentiality of backup data in storage locations and systems.
Knowledge worker Cyber-security safety
We stress the importance of role-based security awareness training for managers, system administrators, and users of organizational systems as well as insider threat awareness training. Testing of staff by simulated phishing attacks should also be conducted with follow up remediation as needed. We provide tools to facilitate both areas as well as dark web monitoring.
Understanding and mitigating legal risks
We will help you identify systems and workflow vulnerabilities, then develop, evaluate and implement mitigation plans and process changes. Implementation and proof of use of cyber security frameworks and standards can provide a path for this objective. We have tools to help you assess, implement, and prove compliance with any major cybersecurity standards or frameworks that your organization is subject to.
Staff productivity and workflow data security
We help you provide your staff the most powerful collaboration, productivity, and data governance tools available. The search features alone can save staff significant blocks of time each day. The tools we provide can help you design secure workflows so data is protected in transit and at rest.
Industry best practices and applicable standards compliance
Whether it is the FTC Safe Guards requirements, ISO/IEC 27001, HIPAA, PCI-DSS, CIS, CCPA, CMMC, or contractual agreements etc. virtually all organizations and companies are subject to demands to protect sensitive private information. We can help you to comply with whatever requirements you are under. Our tools help you identify the sensitive data that resides in your systems and take appropriate action to remove or better secure it.
Total continual compliance as the objective
The bottom line is that we strive to help our clients reach and maintain a high level of compliance to whatever standards you are held to.
Cyber Security and Technology Blogs
Cyber security, technology, and compliance are some of the subjects covered in the filterable and sort able blog grid.
The Mission:
The eUS team is focused on our continuous mission of providing emerging technologies and services to our clients. We are highly credentialed, vibrant, forward-thinking, visionaries who execute and are excited about the future. This passion has persisted through our 20+ year history and it’s not stopping. Since 1998 customers are still trusting us today to keep their business operational. Our customers keep investing in us because of our known excellence for well-managed projects, implementation of disruptive technologies, and seamlessly efficient change transitions. Look to us for your technology future.
The Benefits to our Clients are Significant
- They gain a competitive advantage in the changing global marketplace. This is done with with solutions that are flexible and that scale up as needed. They provide adaptable and affordable communications and workflow architecture.
- Real savings are seen by clients in telecommunications management costs.
- Our clients experience improved employee productivity and efficiency as a result of our solutions and consulting.
- Organizations who use our services and solutions see tangible improvements in customer service and call interaction. This is achieved through better call management and routing tools.

Many Systems, Many Devices, One Provider
Today we carry many devices to conduct our business affairs and lives. Businesses and organizations have always used many systems to communicate. These have gone from traditional desk telephones, cell phones and e-mail to now include instant messaging, conference calls, webinars, faxes and more. We are the premier provider of unified solutions that are designed to address all of your communication needs in a custom solution.
Knowledge and Experience
For many years we have provided Information Technology services and enterprise-enhancing communications solutions. Our clients benefit from the access to our engineering team’s vast knowledge and experience. We have assisted them in developing and deploying several of the largest workflow solution implementations in the nation. These implementations enable our clients organizations to customize the information flow and task assignments throughout the entire enterprise.
Additional workflow solutions offered by eUS provide real-time management of all enterprise connectivity including. These include WANs, WLANs, LANs, Internet, remote office and any enterprise node. regardless of your carrier, mode of connectivity, protocol or location.
Learn About Our Work in These Areas:
- Security & Disaster Recovery:
Our firm can consult with you and implement solutions to help you to prepare to get through disruptions and disasters that come along. Read more about security and disaster recovery issues here. - Cloud Services:
We can help you evaluate how a cloud based solution for voice, data or applications will serve your operation. Read more cloud services information here. - Email Security:
We can help you establish policies and systems to prevent hacking and virus’ infection of your email and networked resources. In addition, the tools monitor your email for things like credit card numbers or SSNs and so on that require sensitive data handling. Read more about email security here. - SDWAN–WAN Optimization:
Our WAN OP work has helped many clients double the amount of data through-put on their WAN and other network data connections. This includes such important functions as off-site backups or data moved between data silos. Read more about WAN OP here. - Voice – IP Telephony
- Business Phone Systems:
We are specialists in office and business VoIP phone phone systems and their complex implementations. We give our clients the benefits of our many years of experience moving from traditional PBX based to VoIP and cloud based voice solutions. More Business phone systems information is here. - Consulting – Services.
- Managed IT Services:
Enterprise US offers Managed IT services for local and wide area networking and voice communications (i.e. VoIP, IP-PBX). In addition to those critical areas of business, we help secure, update and maintain email and line of business applications. See more about managed IT services here.


